Digital security is a key requirement in our product designs, especially in markets such as healthcare where the design is complete long before final regulatory approval. From a commercial point of view, ignoring data privacy, device authentication, and anti-counterfeit at design stage is no longer a tenable position for a connected product that produces sensitive patient data – even if it is nominally pseudonomised.
To support the fantastic healthcare opportunities enabled by digital monitoring systems, there is a need for new security infrastructure, going beyond the healthcare professional ecosystem to not only patients and carers, but their devices.
In future we see the regulatory environment adapting towards approaches adopted by other industries, many of which have successful systems in place to deal with data securely – and this can only increase the importance of digital security in the industry. The challenge is to get over that hurdle before the data leak or hacked device stories take over – which will be too late.
Please can you give an introduction to Cambridge Consultants’ new turnkey digital security platform?
Our system is designed for getting the right security components, such as digital keys, into a medical device or system right at the point of manufacture. That’s the last chance you’ve got to set security ‘cornerstones’ in place that the device will use to authenticate itself during its lifetime, and also to have a ‘digital lock’ in place to protect its data from others.
These components might even be placeholders on product launch, but the important thing is to have them there – they can then support a rich set of data interactions throughout the device’s lifetime – even if some of those features are introduced by an approved software upgrade at a later date.
In the long run these same components determine who’s allowed to see the data produced by the device, and allow the device to digitally prove the origin and even the pedigree of the data that it produces.
The trend is for new digital services and systems to be layered faster and faster onto devices already in the market, and these new services might have security implications. Using our system the devices are ready for them without having to be redesigned from scratch – saving design and approvals cost in the long term product portfolio.
What healthcare applications can Trusted Source™ be used for?
It’s best suited to medical devices that produce patient data, devices that are subject to counterfeiting, devices that need access control by groups of users, or devices that need to authenticate themselves to remote systems as ‘genuine’ or ‘approved’, including those that use wireless standards such as Bluetooth Low Energy or Zigbee.
Some examples might be clinical point of care systems, implantable devices such as pacemakers, or telehealth monitoring systems such as blood glucose meters, panic alarms, pulse oximetry, or blood pressure monitors.
While that usually means devices involving electronics and software, there are also applications for attaching low cost RFID or NFC tags (sub 10 cents) that allow a smartphone or tablet to interact with a non-connected product – this could be to help prove the products authenticity, or perhaps to guide a user straight to an approved software application on a tablet or smartphone.
Why is Trusted Source™ good at supporting low cost security techniques?
The techniques used for digital security across a wide range of industries come in two flavours. The more expensive one – used in bank cards, sim cards, passports, smart metering, automotive and transport, healthcare professional ID cards, even chipped pedigree racehorses – and the cheaper one – used in consumer toys, batteries, and most of the connected medical device industry.
While we’re not saying that these cheaper systems are the optimal design choice for those medical devices, there are nonetheless some steps that can be taken at a 3rd party manufacturing facility to securely manage the required digital keys – which our system is designed to support. Conveniently it’s also good at the more secure versions, which have to be the direction for the future.
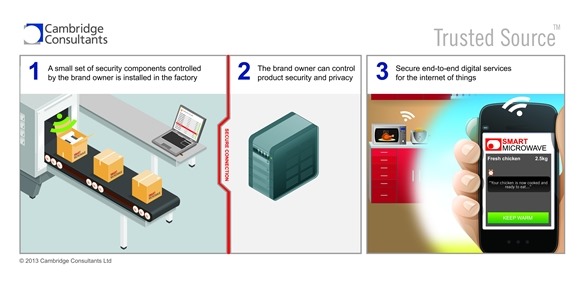
Can Trusted Source™ be customized based on its application?
Yes – while the default is to support secure unique serialisation of devices at manufacture on a production line, particularly when printing codes, or embedding digital keys into chips or secure elements, it could also be modified to distribute keys for use in a smartphone app, provision an HCPs tablet with credentials to access the right patient data, or be an enabler for an end user to digitally check whether a device is genuine, or the pedigree of a pharmaceutical batch. These applications would use the same core components but be integrated into the respective systems.
It’s a tool for setting the right security elements in place at the right time, to support a whole generation of data services, some of which haven’t been invented yet. It’s based on proven best practice in the financial and communications domains, with adaptations for today’s production environments.
For each individual product some limited customisation is required to integrate it with production test software – for that reason we license it as part of an ongoing device development rather than sell it shrink wrapped.
Does Trusted Source™ have any limitations?
If a medical supplier can be fully controlled and audited, with 100% trusted personnel, and 100% trusted business partners, without any counterfeit concerns, and the same applied to each company in each element of the supply chain of that supplier, and you can identify and discount each of the parties that might attack the system in future, then you don’t need Trusted Source™.
More seriously, while it currently runs in a Windows environment on a laptop, with outputs to printers or production test, covering most factory requirements, we are also working towards a secured Linux end-client solution for the Oil and Gas industry.
What plans do the Cambridge Consultants’ software technologies group have for the future?
We’ll continue to supply innovative, proven software into the groundbreaking product developments, server side analytics, data systems, and digital services that delight our clients and their consumers.
And of course we’ll continue to invest in our own new technologies, taking the Cambridge Science Park tradition forward – as a sneak preview, watch out for more from us soon on a low cost Bluetooth Smart sensor for end to end cold chain monitoring of temperature, humidity and shock.
Where can readers find more information?
www.cambridgeconsultants.com
About Jon Edgcombe
 Jon Edgcombe leads the Software Technologies group at Cambridge Consultants. The group designs software across multiple industries, including medical, industrial, consumer, energy, transport and security. Jon specialises in digital security, including ecosystems where multiple commercial parties are involved, or where authentication for low power devices is required.
Jon Edgcombe leads the Software Technologies group at Cambridge Consultants. The group designs software across multiple industries, including medical, industrial, consumer, energy, transport and security. Jon specialises in digital security, including ecosystems where multiple commercial parties are involved, or where authentication for low power devices is required.
Jon’s team leads CCs work on NFC product integration and data frameworks for server side analytics, and is also involved in approved medical device software, Bluetooth smart devices, robotics, and software design review and due diligence.
Alongside software consultancy Jon has led product developments from early design concept to successful market launch, including a novel internet radio, an ultra-wide band radar system for seeing through walls, and sensing technologies for the logistics industry.